October 26, 2023
 by Mara Calvello
by Mara Calvello


Take your business's compliance management to new heights with G2 Track.
There are certain societal expectations everyone follows without question. Stopping your car at a red light. Brushing your teeth before going to the dentist. Covering your face when you sneeze.
The same principle applies to the ins and outs of running a business. A fine or penalty could be around the corner if you don’t comply with specific rules and regulations. Therefore, every company must practice compliance audits and follow the standards that best represent their industry.
A compliance audit is a formal review process that evaluates whether an organization is adhering to laws, regulations, policies, and industry standards relevant to its operations. It's conducted either by internal audit teams or by external auditors and ensures that the organization is operating in a legal and ethical manner.
Compliance audits answer the question, “Is this company doing what it’s supposed to be doing?” The audit report covers the strength of compliance preparations, security policies, risk management procedures, and user access controls over the span of the audit. It fills any gaps in compliance while also making recommendations for ways to solve the issues.
If you want your company to remain profitable and in business for the long term, then knowing the rules and regulations of compliance audits that apply to your industry is a must. Learn more about each type of audit and how G2 Track can help you stay compliant easily.
In business, there are two types of audits that can be confused with each other: a compliance audit and an internal audit. The confusion stems from the fact that they may be conducted by the same person, but they review different aspects of your business.
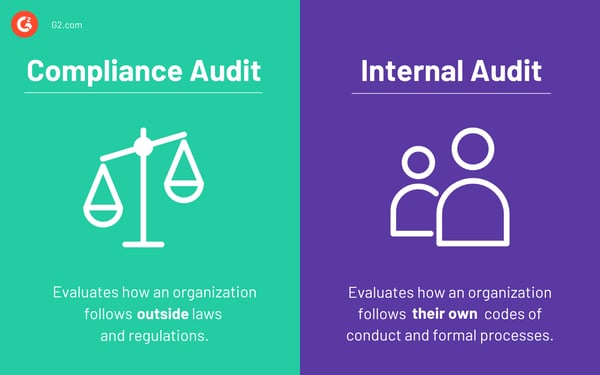
It’s important to keep in mind that an internal audit will gauge how well an organization follows its own internal codes of conduct and formal processes. On the other hand, a compliance audit will evaluate how well an organization follows outside laws and regulations that cover various industries.
Compliance audits serve various purposes in the business and regulatory landscape. The compliance requirements are in place to protect consumers and the industries that serve them. Ensuring that all providers offer the same standards. When businesses fail to comply, this can lead to all sorts of trouble, including fines and, in the worst case, shutdowns.
Here are some key reasons why they are important.
Compliance audits assist in confirming procedures such as:
Regardless of your specific situation, it’s important to have a working knowledge of the types of regulatory compliance audits and what they entail. Below is a list of the most common compliance audits you’ll experience at your organization.
The ISO (International Organization of Standardization) compliance audit is part of the ISO/IEC 27K Series and is an information security compliance standard that helps companies manage the security of assets, such as employee or third-party data, financial information, and intellectual property.
Like SOC 2, the audit involves a risk management process that includes people, processes, and technology. Both standards require that an independent auditor assess a company’s security controls to ensure it's mitigating risks properly.
ISO works with over 160 countries to regulate industry standards as a way to align business practices and resolve any issues that may arise regarding equipment or processes.
One thing to remember about ISO is there’s a difference between being ISO compliant and ISO certified. To be considered ISO compliant, your organization has yet to undergo a formal certification audit. In order to be ISO certified, you will have to undergo a longer auditing process by a third-party who will evaluate your adherence to all ISO standards.
While being certified is voluntary, doing so helps your business increase customer trust and satisfaction.
OFCCP is a part of the U.S. Department of Labor, and it enforces affirmative action and equal employment opportunity requirements for federal contractors and subcontractors.
This compliance law is crucial in promoting workplace equality and preventing company discrimination. It enforces various rules and regulations, conducts audits and compliance reviews, and guides federal contractors on meeting their affirmative action obligations.
NIST was a federal agency within the United States Department of Commerce. It was known as the National Bureau of Standards (NBS) until 1988 when it adopted its current name. NIST has a long history of providing measurement standards, research, and technology development to support various industries and government agencies.
NIST's primary role has been establishing and maintaining measurement and technology standards in the United States. These standards are essential for ensuring accuracy and reliability and promoting innovation and competitiveness in various industries, including manufacturing, technology, and research.
Passed in 1996, HIPAA serves to protect the privacy and security of American’s medical information as a way to reduce healthcare fraud. It also works to ensure coverage for employees who have lost or changed jobs.
If you fall within these types of businesses, it’s up to you to ensure proper measures are being taken to protect health data and that it’s used, shared, and stored correctly internally. There should be technical, physical, and administrative safeguards in place as a way to secure all sensitive information and personal data. If you don’t, fines can reach into the millions depending on the level of negligence.
A HIPAA audit also provides patients with the peace of mind that their private information is secure and never shared with the wrong people.
Tip: Learn more about healthcare compliance and what is required from your business.
Passed by Congress in 2002, the Sarbanes-Oxley Act is mandatory for all public companies.
After major corporate scandals from Enron, Global Crossing, and World.com SOX introduced substantial changes to the regulation of financial practice and corporate governance. The overall goal of this compliance audit is to protect investors by improving the levels of accuracy and reliability of all corporate disclosures.
SOX can be a pretty broad compliance audit. Because of this, both your finance and IT departments need to work together to align their efforts and processes to ensure everything is within the standards. For example, IT departments are required to properly store and manage corporate records. The rules require that there’s no tampering with regulated documents and that they’re properly encrypted and securely stored using the same guidelines as public accountants.
From a financial and management perspective, SOX requires that management teams take responsibility for their own financial records and that specific financial disclosures are made to shareholders, including off-balance-sheet transactions and stock transactions of executives.
If not, the result could be major penalties for the CEO and CFO of your organization.
Payment Card Industry (PCI) compliance is a set of regulations developed to ensure that the credit card industry is properly managing and securing customer data. Before it was formed in 2006, there was no clear industry standard that all credit card companies had to follow, and that's a problem for any company that deals with big data.
The DSS portion of this audit, Data Security Standard, is the regulations being placed on anyone who has to follow PCI compliance.
In 2006, Visa, MasterCard, Discover, and American Express (AMEX) established the PCI Security Standards Council (PCI SSS) to help regulate the credit card industry and establish clear operating guidelines for how consumer credit card information should be handled. These standards apply to any organization that processes payment cards or creates the infrastructure to process payments.
If your company neglects to adhere to these rules and regulations, you could receive a fine of up to $100,000 per month of noncompliance.
SOC 2 is a compliance audit defined by the AICPA (The American Institute of Certified Public Accountants) and is a common compliance standard for modern technology companies. It mainly applies to service providers who store customer data in the cloud. SOC 2 requires these companies to be compliant as they follow strict policies and procedures set in place to protect this private information.
To achieve SOC 2 compliance, most companies prepare themselves for anywhere from six months to a year, including identifying the scope of the audit for their businesses, developing policies and procedures, and putting new security controls in place to reduce risks. Its main focuses are security, privacy, confidentiality, availability, and processing integrity.
SSAE 16 was issued by the American Institute of Certified Public Accountants (AICPA) in April 2010. It became effective on June 15, 2011, and replaced the statement on auditing standards no.70 (SAS 70) for reporting on controls at service organizations.
SSAE 16 was specifically designed for service organizations that provided services that could impact their clients' financial reporting. These service organizations included data centers, cloud computing providers, payroll processors, and other entities that handle sensitive data and perform critical functions for their clients.
The EU’s general data protection regulation (GDPR) is one of the most comprehensive government-imposed data privacy frameworks implemented to date. It went into effect in May 2018 and is meant to protect the data privacy of EU citizens. However, this compliance regulation doesn’t just apply to European companies; anyone who processes the data of European citizens is required to comply.
Today, GDPR auditing is mainly self-driven and follows a four-step process:
Like HIPAA violations, a GDPR compliance violation can come with a pretty hefty fine. Failure to meet these regulations can amount to 20 million euros or 4% of the total annual turnover of the financial year, whichever is higher. If your company deals with or processes data of EU citizens or residents, offers goods and services to EU citizens or residents, or plans to in the future, a GDPR audit could be on the horizon.
CCPA was a landmark data privacy law enacted in California on January 1, 2020. It granted California residents several essential rights related to their personal information. These rights included the ability to know what data was being collected about them, the option to opt out of the sale of their personal information, the right to access and delete their data, and protection against discrimination for exercising their privacy rights.
The CCPA imposed strict requirements on businesses, particularly those with substantial revenue or data collection activities. It empowered the California Attorney General to enforce the law and introduced penalties for non-compliance, impacting how companies managed and protected consumer data in the state.
The CCPA's influence extended beyond California, affecting businesses that operated in the state or collected data from California residents, compelling them to update their privacy practices and disclosure procedures to align with the law's requirements.
Tip: For more tips on how to manage your IT department, check out our comprehensive guide!
If your organization is preparing for a compliance audit, here are some tips to follow – no matter your industry – so you can avoid as many costly fines, penalties, and violations as possible.
Getting a handle on everything to do with compliance can be complicated. With so many rules and regulations to follow, your team should be using a tool that keeps all of your data in one comprehensive and easy-to-read dashboard, like G2 Track.
Since G2 Track brings all of your vendor data, from invoices to renewals and even compliance, into one clean view, nothing gets overlooked. It’s never been easier to stay compliant as you track and evaluate vendor practices, ensuring every application meets industry standards.
Jason B.
G2 Track Review
In addition, G2 Track ensures you know every app in-house with access to employee and company data. This will keep all data close to the chest, making it easy to monitor the activity of all of your users and vendors. This gives you bulletproof evidence of who did what, when, and how.
One of the concerns at larger organizations with hundreds of tools within their tech stack is knowing if they’re staying compliant with how they’re being used, on top of if all of the varying vendors are also remaining compliant.
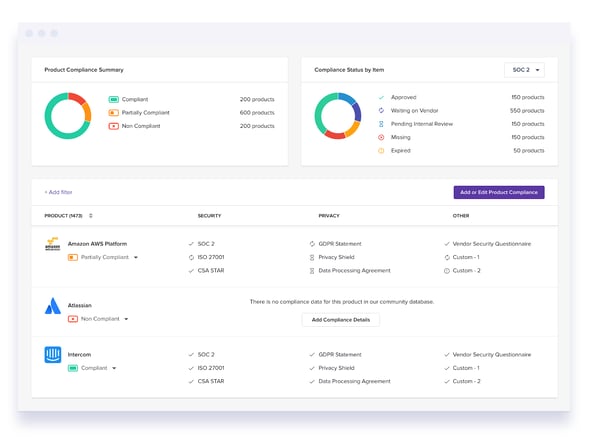
It can be a lot to keep track of, especially if your vendors aren’t publishing their own reports. To make this easier, G2 Track is integrated with its very own Compliance Hub, which helps businesses of all sizes ensure their vendors comply with standards, and it does this all in real time. This helps to eliminate any risk of falling out of compliance because of lost documents, resource constraints, or even human error.
The Compliance Hub is your all-in-one look at everything IT, security, business operations, and compliance, to monitor the data, privacy, security, and company governance of every single product your company uses. G2 Track auto-populates compliance statuses with publicly available data from the vendors you use. This gives you a crystal clear and always up-to-date understanding of the compliance of every application.
Additionally, the G2 Track Compliance Hub:
Just like things change at your company, from new policies to the preferred software, changes happen fast at regulatory agencies. Staying compliant means making an effort to watch for changing enforcement priorities, laws, and regulations before it’s too late.
There are certain things you just need to be prepared for. Take your driver’s test. Running a marathon. And conducting a compliance audit.
It’s in your best interest to look up the requirements to pass and then enforce those requirements as mandatory stipulations in your organization. The smartest way forward is to research the audits that apply to your specific business and see what you need to do to meet the standards -- if you don’t already,
Once you’ve done the research, conduct a self-audit on your business. You can choose to appoint an internal employee to perform the audit, like your organization’s compliance officer, but an independent auditor could be a better option, especially if internal resources are limited. Take the time to have proper documentation and follow-up processes to correct if there are any areas that need to be improved to pass the real audit.
Your business can only be as compliant as the people within it. Because of this, make it a priority to train your employees on what it means to be compliant. Whether your employees are remote or on-site, they need to be fully informed on security policies, what needs to be within financial statements, how personal information is stored or recovered, how to create a strong password, what a phishing email looks like, and more. That way, they’ll be ready for the compliance auditors when the time comes.
It’s clear passing your compliance audit can make or break your company, no matter how small or what industry you’re in. When you know the ins and outs of which audits apply to your business and utilize a tool like G2 Track to keep you in line with the changing standards and regulations, your chances of passing are that much greater.
Passing your compliance audit can save you from paying a pretty hefty fine. Find out more about how G2 Track can help you manage compliance, spending, usage, and more, all while optimizing your tech stack by requesting a demo!
Mara Calvello is a Content Marketing Manager at G2. She graduated with a Bachelor of Arts from Elmhurst College (now Elmhurst University). Mara's expertise lies within writing for HR, Design, SaaS Management, Social Media, and Technology categories. In her spare time, Mara is either at the gym, exploring the great outdoors with her rescue dog Zeke, enjoying Italian food, or right in the middle of a Harry Potter binge.

Take your business's compliance management to new heights with G2 Track.
It’s not very often a business will check in on you after a transaction is made.
 by Mary Clare Novak
by Mary Clare Novak
Big Brother is always watching...to make sure you’re staying compliant.
 by Lauren Pope
by Lauren Pope
If you're in an IT team, you know how the absence of a software license management tool or...
 by Daniella Alscher
by Daniella Alscher
It’s not very often a business will check in on you after a transaction is made.
 by Mary Clare Novak
by Mary Clare Novak
Big Brother is always watching...to make sure you’re staying compliant.
 by Lauren Pope
by Lauren Pope


